Introduction #

Over the weekend, I had participated in USC CTF hosted by University of Southern California.
Here are some writeup of challenges I managed to solve.

It's honest work
Concoction (rev) #
Finally my first rev writeup! (it’s a beginner’s challenge 😅)
An executable file is given, asking for some ingredients to craft a potion.
To solve the challenge, use Ghidra to view the decompiled code. There are a lot of if-else conditions. However,to print the flag, variable bVar1 must be true.
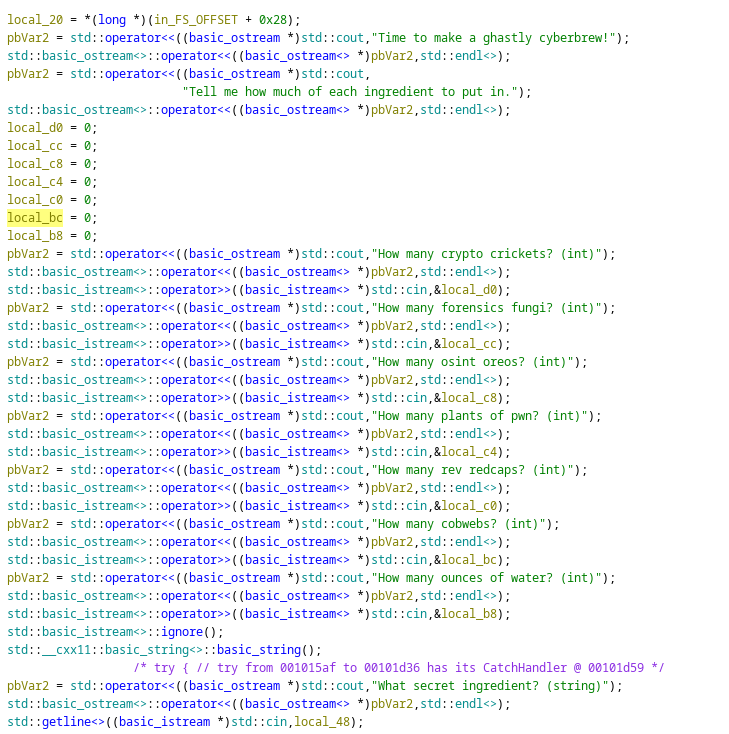
Standard input and the corresponding variables
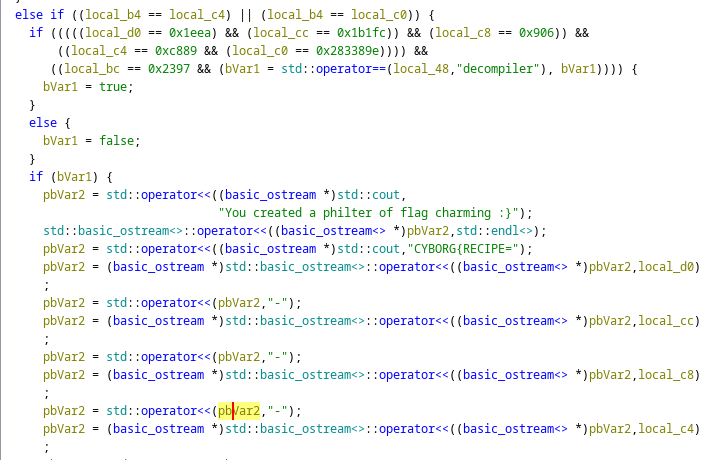
Condition to change bVar1 to true
The conditions to get bVar1 == true is given, therefore, convert the hex values of each corresponding variable into decimal format and insert them when prompted.
- local d0 (crypto crickets) = 7914
- local cc (forensic fungi) = 111100
- local c8 (osint oreos) = 2310
- local c4 (plants of pwn) = 51337
- local c0 (rev redcaps) = 42154142
- local bc (cobwebs) = 9111
- local b8 (ounces of water) = Any number greater than 1 will do
Variable b8 is not a condition, therefore, any value will do as long as it is greater than 0.
The string input prompt in the end must be “decompiler” as it is also one of the conditions.
Solved!
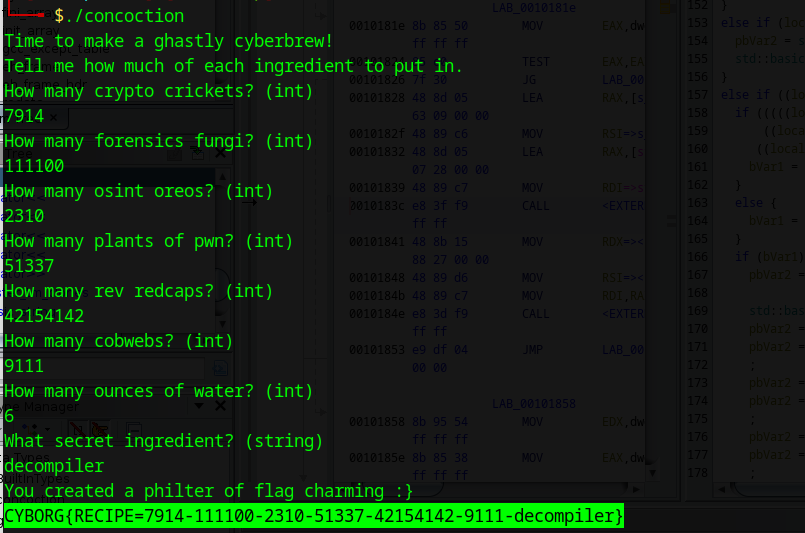
Example of values input(ounces of water does not matter)
FLAG: CYBORG{RECIPE=7914-111100-2310-51337-42154142-9111-decompiler}
Tommy’s Artventures (Web) #
An URL is given, which redirects to an AI art page. In order to login to the page, create an temporary account.
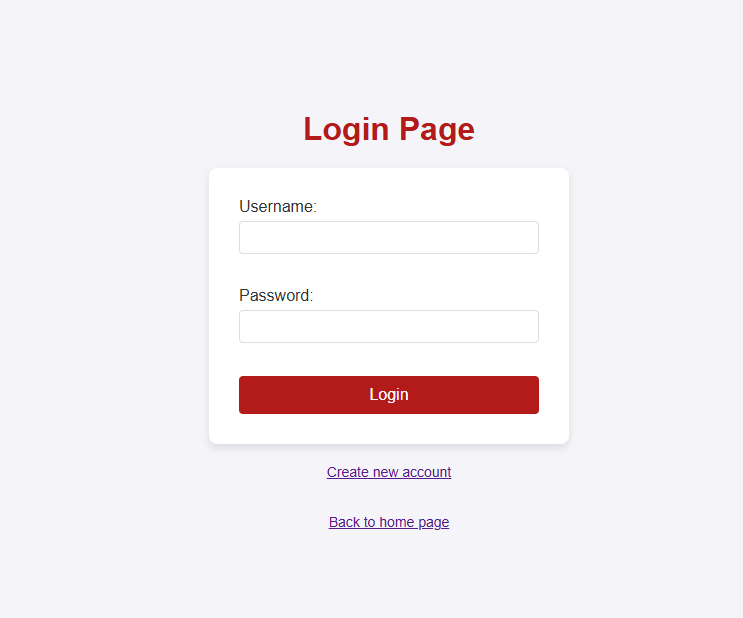
Login Page
During the navigation to “curate” page, a messaged shown indicating the login user must be admin.

Message in Curate page
Based on the secret key attached in the challenge, it is clear that reforging of the session cookie is required. Firstly, copy the cookie from “Inspect > Application and decode the cookie to check the format. (There is another way using Burpsuite, but I am not sure how 😅)
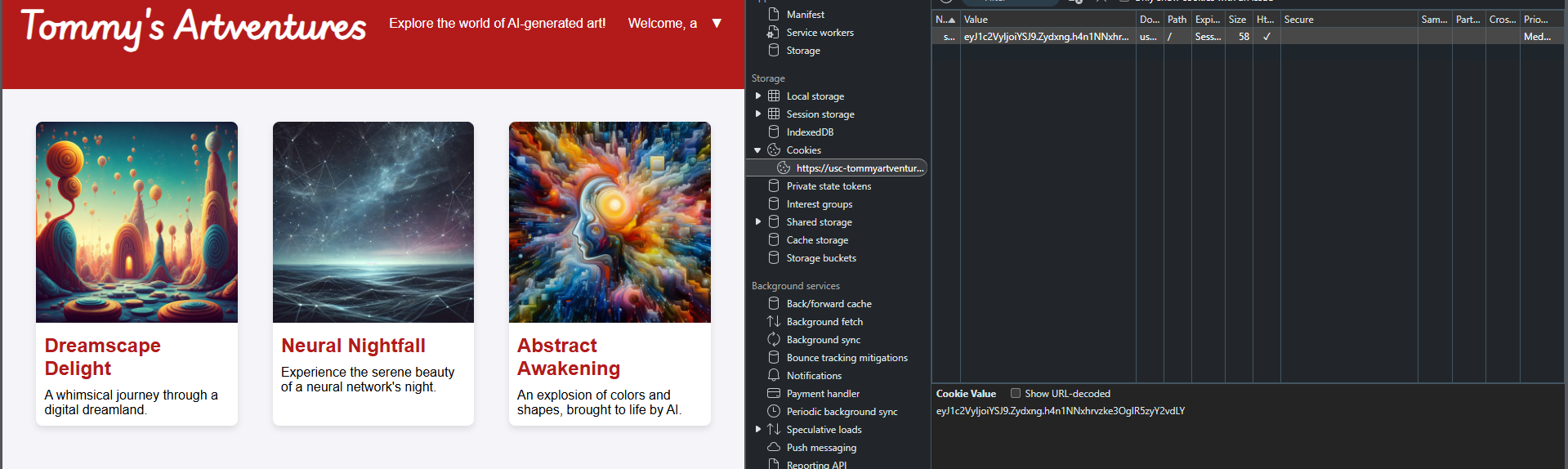
Find the cookie in "Inspect"
To create a new cookie, I used this website as a reference, and the CLI command is attached below. (Remember to install the tool first)
pip3 install flask-unsign
flask-unsign --sign --cookie "{'user': 'admin'}" --secret 'THE-SECRET-KEY'
After changing the forged cookie, the session is currently logged in as admin, and the flag is found in the ‘curate’ page.
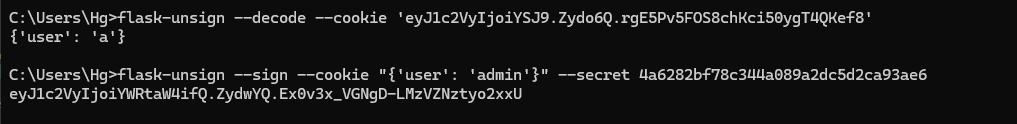
Decode and sign cookie using flask-unsign tool
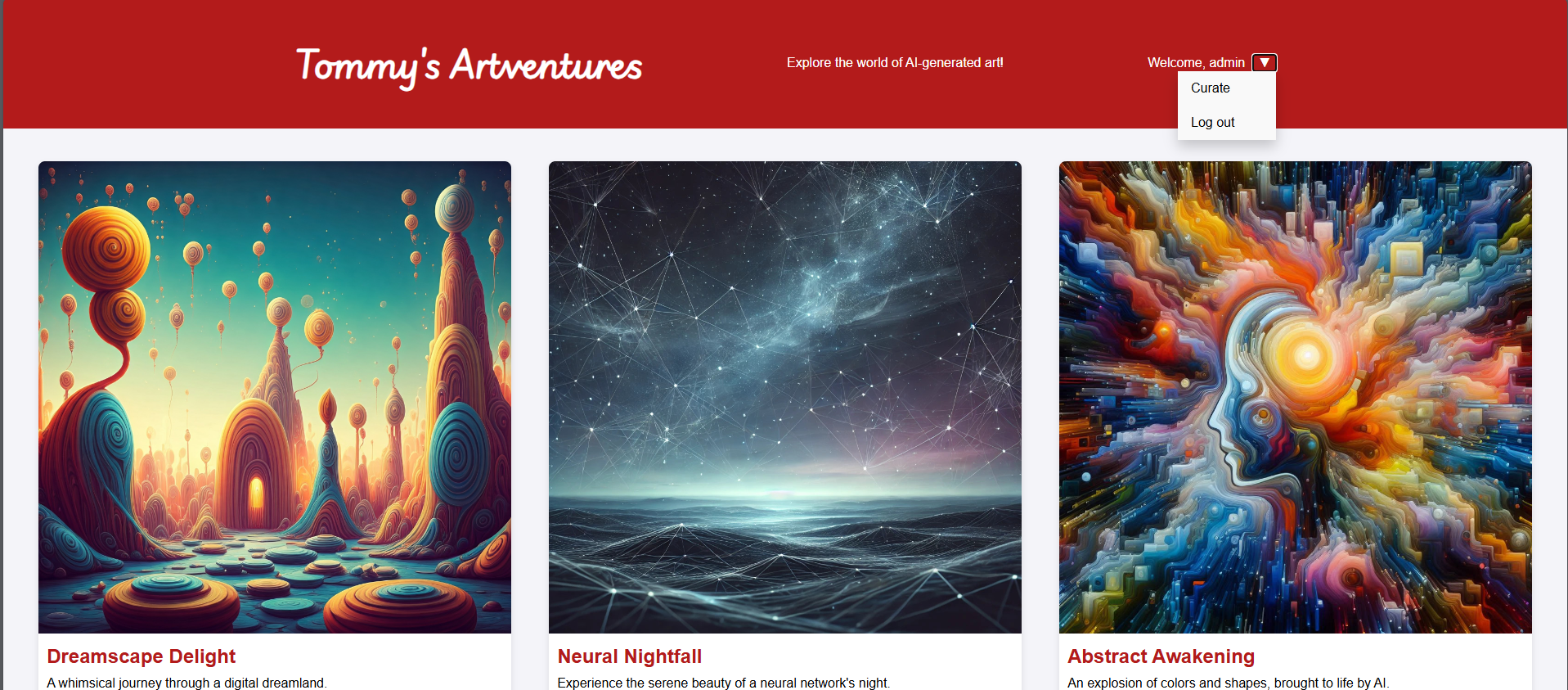
Successfully logged in as admin
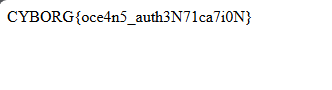
Flag is shown in "Curate" page.
FLAG: CYBORG{oce4n5_auth3N71ca7i0N}
Buildings (OSINT) #
A pdf file was attached with contents of buildings, and I assumed that these buildings are in USC.
The flag format is CRYPTO, therefore no investigation is needed for the first 6 pictures (pictures before the curly braces).
These are the names of the buildings for the flags, index them accordingly using their acronyms, and the flag is found!

BRI

CKS
FLAG: CRYPTO{BRICKS}
RedWoods (misc) #
A .jar file is attached.
Use WinRAR to unzip the jar file. There are 3 files inside.
To open the class file, use an online Java decompiler to decompile and view the Main.class file.
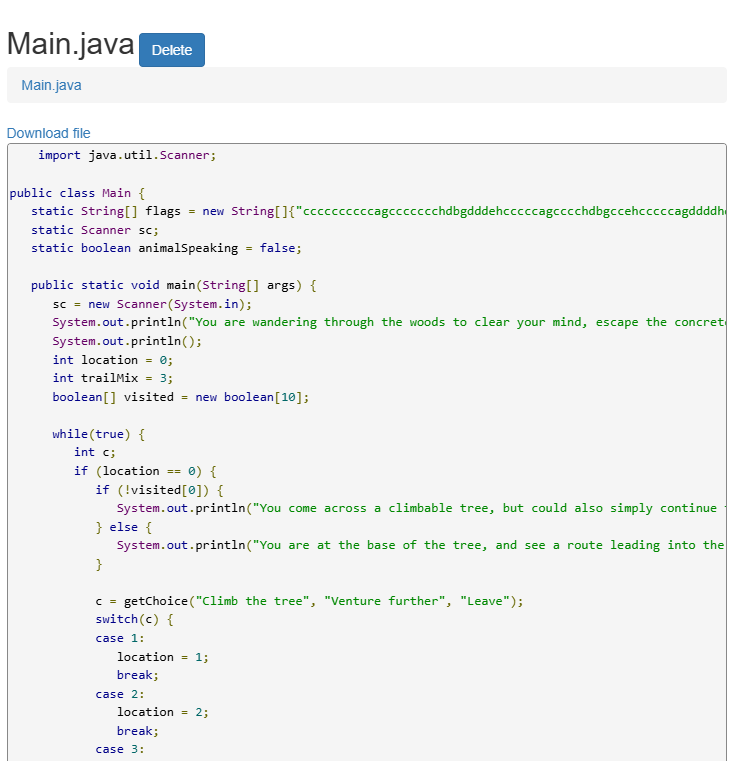
Decompiled code
After going through the code, the code does nothing much by just printing out the message in the flags array. Therefore, the flag is assumed to be in this array.
static String[] flags = new String[]{"ccccccccccagccccccchdbgdddehcccccagcccchdbgccehcccccagddddhdbgdddehgcccccccccccccecccedddddddd", "dddeagcgchhdbcccccagcccccccccchdbgccegcedddeddddeccccccccccccccccceddddddddddddddehhccccccaggccccchhdbggdddeddddddddddde", "ddehhccccccaggdddddhhdbggdeehhcccccccccccaggcccchhdbggehhcccccaggdddddhhdbggeagcgchhdbabccccccaggdddhhdbggehcccccceehhcce"};
Combine all three array elements together to form a long string. However, the string does not mean anything after analyzing with Cipher Identifier.
Next, use AperiSolve to analyze the image. There is a hidden message. By looking at the symbols, it is easily identified as the Brainfuck cipher.

Hidden message (Is it the reason of the naming for the challenge?)🤔
Use any word editor to replace the alphabets with the symbol given, and decrypt the new ciphertext. The flag is found!
Brainfuck message as below:
++++++++++[>+++++++<-]>---.<+++++[>++++<-]>++.<+++++[>----<-]>---.<>+++++++++++++.+++.-----------.[>+>+<<-]+++++[>++++++++++<-]>++.>+.---.----.+++++++++++++++++.--------------.<<++++++[>>+++++<<-]>>---.-----------.--.<<++++++[>>-----<<-]>>-..<<+++++++++++[>>++++<<-]>>.<<+++++[>>-----<<-]>>.[>+>+<<-][]++++++[>>---<<-]>>.<++++++..<<++.
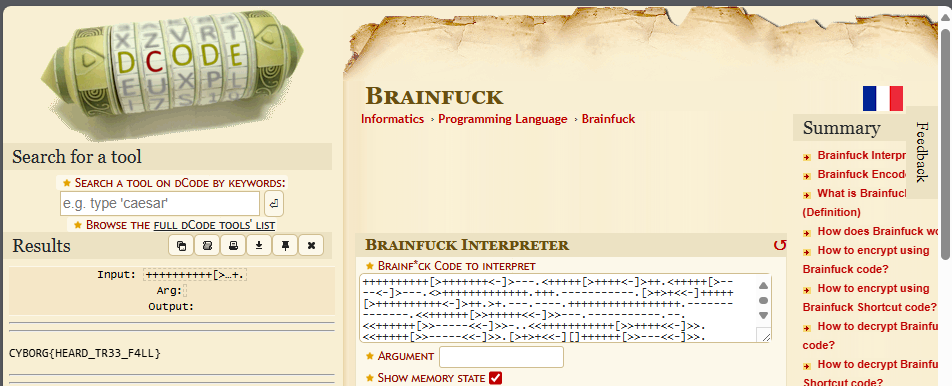
Decrypted Message
FLAG: CYBORG{HEARD_TR33_F4LL}
Conclusion #
Overall, the CTF contains various challenges suitable for players from different levels. Some challenges were really out of my knowledge. I will try to understand them and do better next time. (I got rank 79th btw)
Anyway…
